CORPORATE GOVERNANCE
Han Ke Yuan attaches great importance to information security and customer privacy. In order to effectively prevent information leakage and loss, we refer to the information cycle in the nine cycles of internal control and formulate corresponding measures to ensure the confidentiality, integrity and availability of information. The Administration Department is responsible for information security related matters, comprehensively planning, deploying, maintaining, designing and reviewing related information security management matters, and regularly reporting to the governance level on the plans, development directions and progress of the relevant information systems to enhance the overall information security capabilities of Hanco.
In order to maintain the company's competitive advantage, all employees should comply with the relevant information protection measures issued by the company and have information security awareness. Hanco has formulated the "Computer Account and Official Computer Usage Specifications" to effectively manage employees' account access rights and ensure the safe use of physical assets and software. We require employees to sign computer property regulations so that relevant departments can assist employees in installing relevant software and settings.
Hanco is committed to ensuring information security. It not only focuses on formulating corresponding measures and implementation rules, but also actively promotes employees' information security awareness and self-management. Through these efforts, we have improved our overall information security protection capabilities to ensure the company's business operations and competitive advantage.
In general, although Hankeyuan has not purchased information security insurance for the time being, through the operation of the information security department and the implementation of information security policies, it can still provide a safe and secure information security environment to ensure the information security of the company's various services. The subsequent goal is to complete the company's internal information security expert system to strengthen the company's information security protection network and establish an information security joint defense mechanism. In addition to expanding the number of information security talents in the future, we plan to carry out training and certification work to make the company's information security more complete and trustworthy in terms of manpower and capabilities.
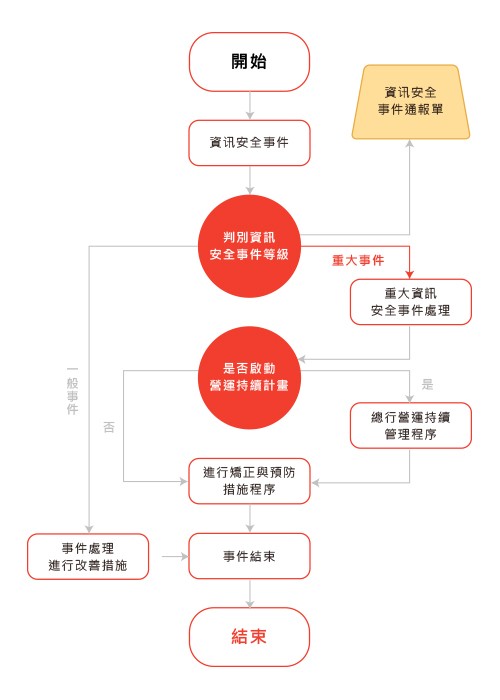
Han Ke Neng Yuan Information Security Operation Process
In order to maintain the company's competitive advantage, all employees should comply with the relevant information protection measures issued by the company and have information security awareness. Hanco has formulated the "Computer Account and Official Computer Usage Specifications" to effectively manage employees' account access rights and ensure the safe use of physical assets and software. We require employees to sign computer property regulations so that relevant departments can assist employees in installing relevant software and settings.
Hanco is committed to ensuring information security. It not only focuses on formulating corresponding measures and implementation rules, but also actively promotes employees' information security awareness and self-management. Through these efforts, we have improved our overall information security protection capabilities to ensure the company's business operations and competitive advantage.
- Each unit of the Information Management Center has established a list of relevant information assets, clearly identified the owners, and continuously implemented various control measures.
- Relevant personnel must undergo necessary assessments and sign relevant work regulations when they are hired. Their information assets must be returned when they are transferred or leave the company. Both new and current employees must participate in information security education and training to enhance their awareness of information security protection.
- Access control should be implemented for entry and exit of company buildings and information security controlled areas.
- Colleagues are strictly prohibited from setting up network equipment to connect external networks and the company's internal network without permission. Both internal and external networks are protected by firewalls, demilitarized zones (DMZs), and necessary security facilities. Important equipment should have appropriate backup or monitoring mechanisms to maintain its availability. Employees should install anti-virus software on their personal computers and regularly check for virus code updates. The use of unauthorized software is prohibited.
- Employees should take responsibility for the safekeeping and use of their personal accounts, passwords and permissions; management personnel should conduct regular audits and reviews; important system operation data should be backed up and restored from time to time.
- System development should consider the establishment of security control mechanisms at the initial stage, strengthen control and contract information security requirements for outsourced development, and evaluate the control requirements of the system so that necessary controls can be taken.
- Colleagues should report any information security incidents immediately and cooperate with the responsible department to resolve them.
- Employees should implement a confirmation and review mechanism in their daily work to maintain data accuracy. Supervisors should supervise the implementation of the information security compliance system and strengthen employees' information security awareness and legal concepts.
Information security management specific management plan
In addition to the company's administrative department being responsible for coordinating, managing and supervising all cybersecurity business of the group, the company also has dedicated cybersecurity engineers to handle cybersecurity work, conduct regular vulnerability scans, protection system effectiveness checks and other related cybersecurity tests, and provide relevant cybersecurity promotion and education and training courses; Han Keyuan will also recruit internal information engineers in 2023 and plans to organize cybersecurity education training and promotion.In general, although Hankeyuan has not purchased information security insurance for the time being, through the operation of the information security department and the implementation of information security policies, it can still provide a safe and secure information security environment to ensure the information security of the company's various services. The subsequent goal is to complete the company's internal information security expert system to strengthen the company's information security protection network and establish an information security joint defense mechanism. In addition to expanding the number of information security talents in the future, we plan to carry out training and certification work to make the company's information security more complete and trustworthy in terms of manpower and capabilities.
Han Ke Neng Yuan Information Security Operation Process
